Fifty years ago, on July 16, 1969, the Apollo 11 lunar mission sent the first astronauts to the surface of the moon. The computing technology used on that Apollo mission was revolutionary. The astronauts could control the spacecraft through a command module computer, and critical safety and propulsion mechanisms were controlled by software for the first time. Today the computing technology of the average cell phone far exceeds the computing power of the spacecraft that got humans to the moon and home safely. A single iPhone could guide 120 million Apollo era spacecraft to the moon, all at the same time!
With that kind of computing power in our pockets, it is no wonder so many of us take advantage of numerous mobile applications, social media, messaging, and collaboration workstream tools as often as we do. On average, each of us spends 4 hours a day staring down at our phone, often blurring the lines between business and private communications.
The universe of discoverable ESI (electronically stored information) is evolving rapidly. For many organizations, within three years of adopting an enterprise-level workstream collaboration platform, the volume of new data generated from that platform will eclipse the amount of data generated by email. Notably, Microsoft Teams is quickly becoming Office 365’s main collaboration tool and is on pace to become as prominent as Outlook. Messaging data and social media communications are routinely implicated in discovery requests and, with increasing regularity, submitted as critical evidence in legal proceedings. Data collections and discovery requests involving mobile, messaging, and collaboration applications often involve personal data and PII (personally identifiable information). Sensitive personal information might be there unintentionally, due to the nature of the applications for keeping people connected and perhaps a business culture that comingles business and personal lives. Other reasons may include the frequency at which many of us increasingly use these applications outside the traditional 9-to-5 workday and a lack of corporate guidance or use policies for new and emerging technologies.
There is no doubt that redefining our eDiscovery processes, methods, and approaches is necessary for new technologies and the ESI they generate. Potentially responsive information likely exists in the candid communications common to messaging or collaboration applications, such as in chats, on virtual “white boards,” and in edited and re-edited versions of documents. But getting to this information, and along the way mitigating risks for personal data protection, is easier said than done. Emerging technologies are dynamic, context sensitive, and multi-dimensional. Every new content source requires its own method of collection, and they all behave just a little differently. It is likely that organizations will increasingly select discovery tools that can collect and process data across multiple cloud technologies or applications. This will ensure a reliable, defensible method of collection and processing compatible with conventional eDiscovery workflows already in place.
The implications for privacy and data protection, though, are considerable. Myriad multi-jurisdictional regulations require a balancing act to protect the data privacy of individuals while simultaneously meeting obligations for discovery. These regulations, such as the EU’s General Data Protection Regulation (GDPR), the Health Information Portability and Accountability Act (HIPAA), and the now imminent California Consumer Privacy Act (CCPA), cannot be ignored. A raised consciousness and awareness of privacy protections in discovery is required, in parallel with efforts to preserve and produce relevant, discoverable ESI with efficiency and precision. A serious regulatory risk exists for unintended personal data – particularly health or other similarly sensitive information – which may somehow find its way into collection and discovery. The risk is heightened when the appropriate data minimization controls have not been implemented or even considered, resulting in personal data being swept up in overly broad collection exercises.
The challenge of protecting personal data is increasingly being addressed by eDiscovery workflows designed specifically for mobile data and ESI from collaboration applications. Although these solutions are at a relatively early stage of development, well-defined guidance is available for how to embed data protection across workflows without sacrificing existing road-tested best practices, i.e. Privacy by Design.
The Privacy by Design concept has been around for quite a while, with inception as a Canadian thought experiment in how to ensure data protection across emerging technologies. But it has now been codified in Article 25 of the GDPR. Privacy by Design provides a solid roadmap for how to build data protection compliance into a product or workflow from the ground-up, as opposed to shoe-horning requirements into a process after it has already been developed. Privacy by Design-based approaches for discovery seek to integrate personal information protection over the lifecycle of all data handling processes. Importantly, the focus is on adaptation and evolution, not a zero-sum game that trades capability for over-restrictive data protection measures. Key attention is accordingly placed on relevance and materiality, from data collection through production, across the entire EDRM (electronic discovery reference model).
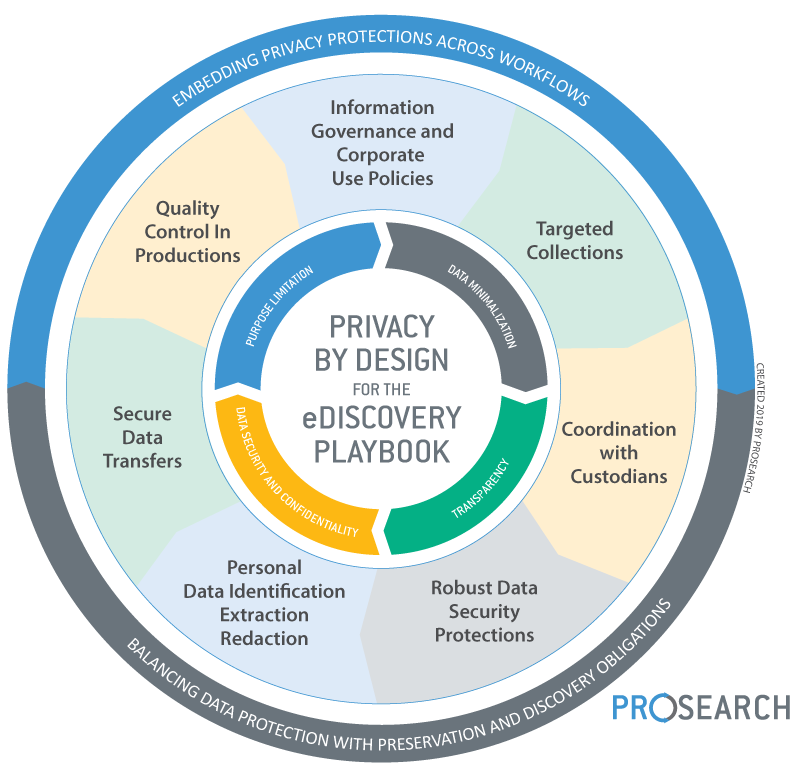
In practice, Privacy by Design throughout discovery could be as follows (see illustration):
- Information governance
- Privacy compliance and legal teams become engaged when new content sources are evaluated for business use. These teams ensure that data collection can be carried out in a defensible way and that it incorporates security measures and data protection considerations, thus demonstrating accountability and a thoughtful consideration of these issues.
- Well-defined use policies and clear requirements for employees are then implemented for enterprise devices and apps, particularly as processes and protocols evolve for eDiscovery.
- Coordination with custodians
- A collection process for more detailed, nuanced coordination with custodians is established – perhaps including some measure of self-collection for certain applications. However, self-collection will require a level of due diligence and assurance that the collections proceed properly, involving the right data, from the right custodian, for the right matter. In most cases, well-articulated, streamlined coordination with custodians will enable further insights into what unintended personal data or personal health data might be implicated in a collection. Again, this type of approach demonstrates accountability, a compliance requirement that could be crucial in the event of regulatory oversight.
- Extracting personal data from data sets
- As data moves across the EDRM and enters into processing, review and production, solutions for indexing, entity identification, and extraction aimed at removing, redacting, or otherwise disposing of any non-necessary personal data, ahead of even the review process, may significantly mitigate risk.
- As an added measure, this same entity identification/extraction process can be replicated and reused for data subject access requests and breach responses, further enhancing the organization’s regulatory compliance posture.
- Smart productions
- At the very last stage of the discovery process, production quality control can serve as a last line of defense in eliminating non-material or unintended personal data. An emphasis on flawless productions is not only an essential part of the workflow, but should serve as the endgame of a truly well-developed eDiscovery playbook. The goal is to show every effort being made to ensure accountability for data protection compliance.
- Data security across processing activities and transfers
- It is absolutely necessary – at every stage of discovery – to ensure that technical and organizational measures for security and data protection are in place, including access controls, security processes, audits, and data transfer protections. Security protections are critical regardless of whether data is processed, hosted, reviewed, and ultimately produced in the EU, United States, or anywhere else. Data security can be the common thread for assuring data protection compliance across numerous regulatory frameworks, as well as for data transfers in cross-border litigation and investigations.
Our shifting global regulatory landscape for data protection, together with exponential growth in the use of mobile applications and collaboration workflow tools, is changing the way data collection is approached, how data is handled, and how organizations will be held accountable for the treatment of personal and sensitive data in the discovery process. Solutions will require a re-consideration of conventional approaches to forensics, data collection, and eDiscovery workflows.
Privacy by Design offers a useful model for embedding privacy protections into the discovery process. It enables organizations to chart a course in the new universe of data, including development of well-crafted information governance processes for new and emerging technologies, focusing on privacy risk mitigation throughout the EDRM, and ensuring an emphasis on data security each step of the way.
Technology doesn’t wait for anyone. While only 50 years separate the computers of the Apollo mission from today’s iPhones, the pace of technology advancement is exponential. eDiscovery processes must keep up.
