Hey there, cyber sleuths! TechnoCat, Cat Casey, here, ready to uncover some digital secrets! As we’ve chatted before, eDiscovery is the Sherlock Holmes of the digital age.
It’s a wild ride through the backroads of electronic data, hunting for clues, securing them, and sometimes even scrutinizing them under the high-tech lens of AI. All this to achieve our grand goal: serving justice by using this data as evidence.
But when our journey crosses paths with PII, or Personally Identifiable Information, the plot thickens. The stakes? Sky high, my friends. We’re not just talking about the outcome of a legal case, but the very fabric of people’s privacy.
Fear, Desire and PII
As we dig through the digital world for clues, we must treat PII as though it were made of glass. This game isn’t just about solving the mystery, it’s about protecting the privacy of individuals involved.
Imagine this: a company is caught up in a legal tangle and they’re going through the rigmarole of eDiscovery. They can’t just broadcast their customers’ or employees’ private info to the world, right?
Because eDiscovery often means wading through sensitive PII, it’s like a treasure chest for potential data breaches or unauthorized prying eyes. It’s crucial that we defend the castle, protecting the personal identifiers of data subjects, custodians, and others involved in the process.

Golden Rules for PII in eDiscovery
Ready for some PII in eDiscovery secret sauce? the golden rules for keeping PII, or Personally Identifiable Information, safe and sound during our investigations?
Here are the commandments to swear by for protecting PII during the eDiscovery marathon.
- Scope it Out: As with any mystery, know your cast of characters. Conduct comprehensive data mapping and understand the landscape of your PII. No self-respecting detective goes in blind.
- Sort with Sophistication: Organize your data based on its sensitivity, using a slick data classification framework. Think of it as sorting your evidence locker.
- Controlled Access: Just as we wouldn’t let anyone traipse through our crime scene, we need to safeguard the vault of PII in our document review datasets. Cue in Role-Based Access Control (RBAC) or Attribute-Based Access Control (ABAC).
- Cipher Mysteries: Keep PII cloaked with encryption. It’s our secret handshake in the world of codes.
- Redaction Action: When the time comes to share, use advanced redaction tools to keep the private stuff private. Imagine it as a sensor bar for sensitive data.
- Audit Trails: Leave a digital paper trail with robust auditing and logging systems. Show who snooped where and when. Remember, detectives are nothing without their notebooks!
- Security by Design: We don’t just stick our security measures on top; we weave them into the fabric of our eDiscovery process. That’s our mantra of Security by Design and by Default.
- Stay Up to Date: Keep our protective gear sharp and shiny – timely patches and updates to our data protection software are a must. After all, even our high-tech gizmos need a little TLC!
- Continuous Learning: Keep that gray matter ticking with regular training on the latest PII protection techniques. A true detective is always learning!
- Incident Response Plan: Always have a Plan B for those unexpected plot twists – a ready-to-go Incident Response Plan for the dreaded data breach moments.
Why Should I Care About PII?
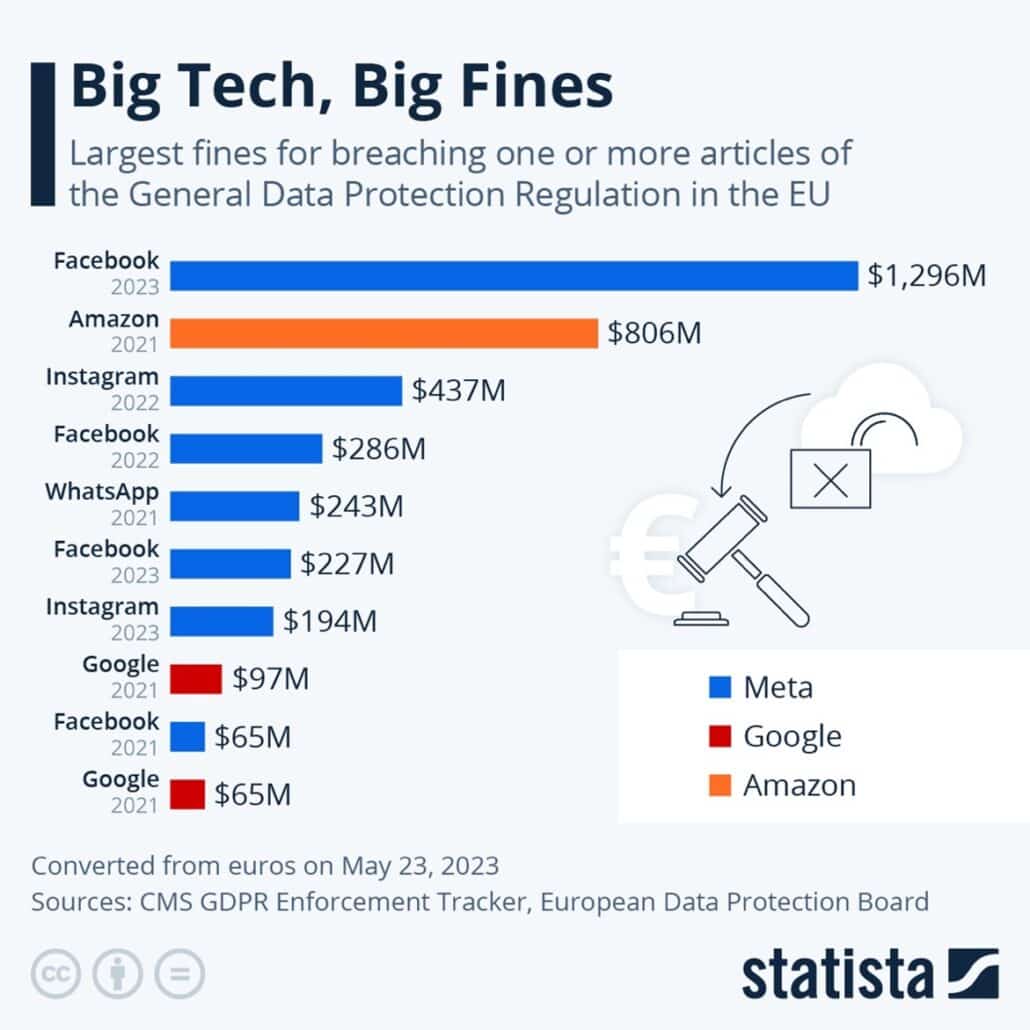
But why is all this so important? It’s not just about being nice; it’s a must-do, mandated by data privacy laws worldwide. The heavy hitters are the General Data Protection Regulation (GDPR) in the EU and the California Consumer Privacy Act (CCPA) in sunny California. Many other regional laws also insist on the kid-glove treatment for PII. It’s not optional, it’s the law.
When it comes to safeguarding personal data during the eDiscovery process, we must pull out all the stops and ensure strict adherence to data protection laws and regulations. Donning our data protection cap, we must be vigilant in handling various types of data that may contain sensitive information qualifying as personally identifiable information (PII).
Let’s not underestimate the repercussions of mishandling PII, especially in different jurisdictions. In the European Union, violations of the General Data Protection Regulation (GDPR) can result in substantial fines of up to 4% of a company’s global annual turnover or a hefty €20 million—yikes!
But wait, there’s more! Closer to home, the California Consumer Privacy Act (CCPA) takes center stage with potential fines of up to $7,500 per violation. Trust me, those fines can quickly pile up and deliver a significant blow to your bottom line.
Just as a heads-up though, health-related data, or Personal Health Information (PHI), plays by its own rules and regulations like HIPAA, not to mention GDPR and CCPA.

Guardians of the PII Galaxy
So, as we don our digital detective hats and dive into the vast sea of data, let’s remember to tread lightly. We’re not just investigators, we’re also protectors of personal data. Remember, we’re not just digital detectives. We’re also guardians of personal privacy. Until our next digital adventure, this is TechnoCat, signing off.
Stay savvy, folks!
Interested in ACEDS’s educational content? Subscribe to the ACEDS Blog for weekly blog updates: https://aceds.org/aceds-blog/


